www.industryemea.com
16
'24
Written on Modified on
CYBERTHREATS FOR 2024 – NAVIGATING THE UNPREDICTABLE
Dr Shekhar Pawar explains how SecureClaw helps companies navigate cyberthreats for 2024 by tracking cyber-attack statistics of 2023.

Dr Shekhar Pawar
SecureClaw Cyber Threat Advisory, which keeps an eye on daily cyber threat news and alerts and tries to recommend solutions to companies worldwide, has studied more than 4,500 pieces of cyber news from across the world, appearing in leading cyber news forums and websites. Here are a few important statistics that are the outcome of the compilation of cyber news worldwide, considering the period from January to December 2023. Geography-wise, this data may differ from the actual cyber-attack statistics of a few countries, as at the ground level, many organisations from a few countries never report cyber incidents to authorities or news channels. Whereas the eagle eyes of our cybersecurity experts from SecureClaw have captured maximum cyber-attack news from many countries, it will give more insights about types of cyber threats and related information.
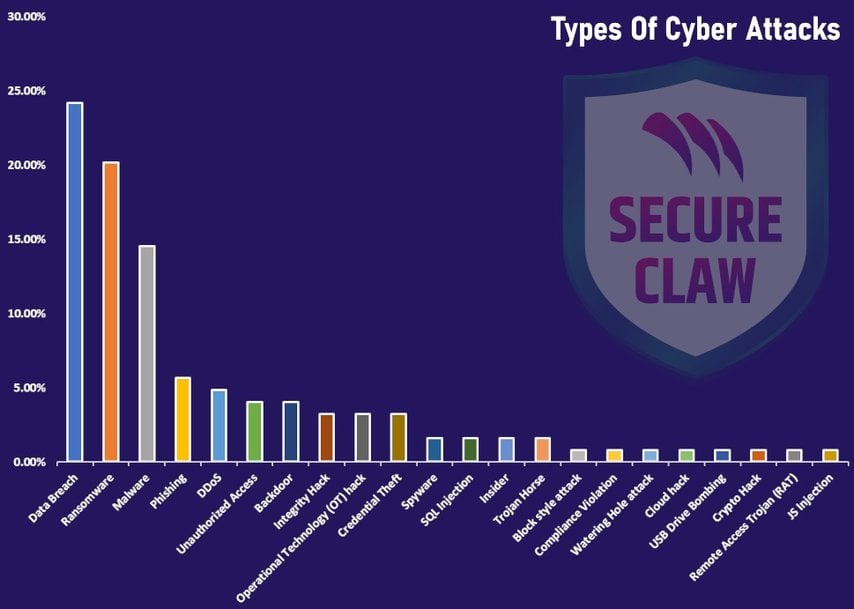
The various types of cyber-attacks
Key observations by SecureClaw
Apart from various industry domains, a few domains, such as automobiles, manufacturing, software providers, cloud providers, energy, telecom, healthcare, crypto, government, hospitals, pharmaceuticals, gaming, shipping, aerospace, and a few service providers, were mostly on the radar of cybercriminals throughout entire 2023. Most cyber threats were targeted at database systems, IT infrastructures, software systems, operational technology (OT), websites, servers, computer machines, emails, the cloud, APIs, ChatGPT, and mobile apps. Different techniques and sophisticated cyber-attacks were used via various types of data breach methods, including ransomware, malware, phishing, DDoS, unauthorised access, backdoors, integrity hacks, operational technology (OT) hacks, credential theft, spyware, SQL injection, insiders, and Trojan horses. The purpose of these cyber-attacks can be summarised as damaging reputations, disrupting business activities, hurting the competition’s business, extortion (financial demands), or illegal or unauthorised access to data. Also, few cyber-attacks seem to be state-sponsored, as there are wars and conflicts going on across the borders of a few countries.
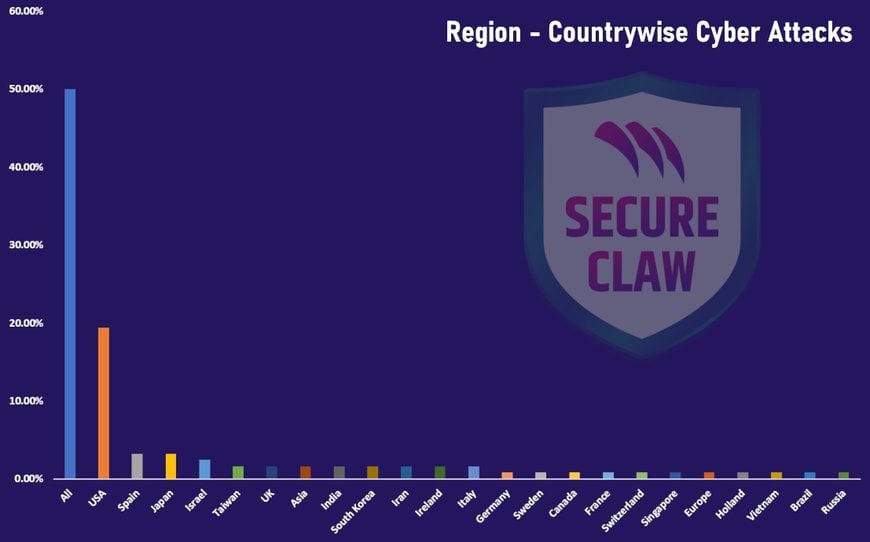
Region-countrywise cyber-attacks
More advancement in cyber-attack techniques
Ransomware attacks in 2023 had negatively impacted a few large enterprises, including automobile companies Ferrari, Tesla and Volvo Cars; maritime information services company Royal Dirkzwager; Hitachi Energy; Taiwanese PC company MSI; the Suzuki motorcycle plant; multinational tech firm ABB; Japanese pharma giant Eisai Group; Spanish bank Globalcaja; chip giant TSMC; Japanese watchmaker Seiko; Johnson Controls; MGM casino; Chilean telecom giant GTD; British Library, and the attack on a South Korean anti-aircraft weapons system.
During these months, PlayCrypt (Play ransomware), Clop ransomware, Vice Society ransomware, Black Basta ransomware, LockBit ransomware, BlackCat/ALPHV ransomware, Snatch ransomware, Rorschach ransomware, and Rhysida ransomware were among hundreds of ransomware gangs that were more active in sophisticated cyber-attacks. Each of these ransomware gangs has a typical pattern they have developed for performing cybercrimes. Since June 2022, multiple victims of Play ransomware assaults have surfaced in Bleeping Computer forums. The ransomware named Play gets its name from the way it encrypts files: it adds the ".play" extension afterwards. The group's email address and the solitary word "PLAY" are also included in the ransomware note which is a unique pattern followed.
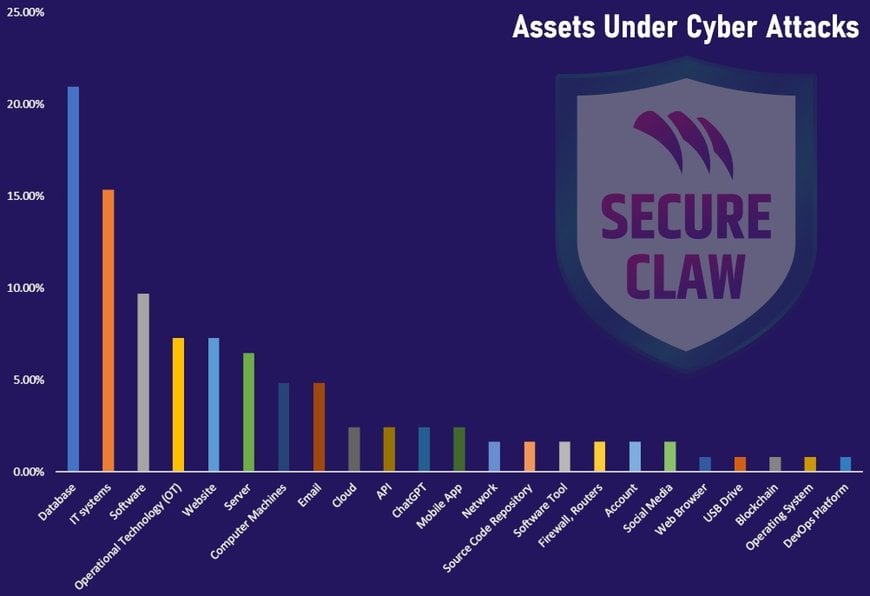
Assets under cyber-attacks
The Russian ransomware group Clop is well-known for its demand that victims pay millions of dollars before disclosing information that it says it has compromised. Vice Society is the next Ransomware-as-a-Service (RaaS) attacker targeting the education industry; move over, Lockbit. Vice Society is thought to be an extortion, exfiltration, and intrusion organisation with Russian roots. Vice Society is well-known for, like many other ransomware groups, stealing data from victims' networks prior to encryption in order to use it for double extortion. They then threaten to post the data on the dark web if the demanded ransom is not paid.
The Black Basta ransomware group, which has been active since April 2022, has been seen attacking American companies, concentrating mostly on the manufacturing and construction sectors. They have also been seen focusing on the real estate, food and beverage, chemicals, insurance, healthcare, and mining and metals industries, as well as business services. Malicious malware known as LockBit ransomware which encrypts files, renders them inaccessible, and demands payment for the decryption key. LockBit will automatically scan a network for worthwhile targets, disseminate the malware, and encrypt every machine that is reachable. Highly targeted attacks on businesses and other organisations are carried out by this ransomware.
Originally appearing in November 2021, BlackCat is a family of ransomware written in Rust, also going under the names ALPHV and Noberus. It also happens to be the name of the threat actor or actors that take advantage of it. BlackCat uses the RaaS business model, wherein the malware's creators provide it to affiliates for use and keep a cut of any money received in ransom. The Snatch ransomware, formerly known as Team Truniger, initially surfaced in 2018. Using RaaS, Snatch charges other threat actors for the ransomware payloads they supply. Snatch further employs double extortion by gaining access to their victims' private information. Snatch presses their victims to pay the ransom by threatening to expose the stolen material to the public if the requested ransom is not paid.
BabLock, also known as Rorschach, is a ransomware that has been making waves lately because of its fast-moving, sophisticated assault chain that employs deceptive yet powerful strategies. This ransomware was found to use an unusual method of attaching extensions in June 2022. Investigators found that, in contrast to the standard ransomware assault strategy of "one sample, one extension," the attackers for this particular infection were appending numerical increments ranging from 00 to 99 on top of the preset ransomware extension. Because of this, several extension versions may arise from a single execution even on an infected machine. Rhysida is a ransomware operation that targets Windows systems. It gained notoriety in May 2023 when it was connected to several high-profile cyber-attacks that occurred in Western Europe, North and South America, and Australia. There seems to be a connection between the group and the infamous Vice Society ransomware group.
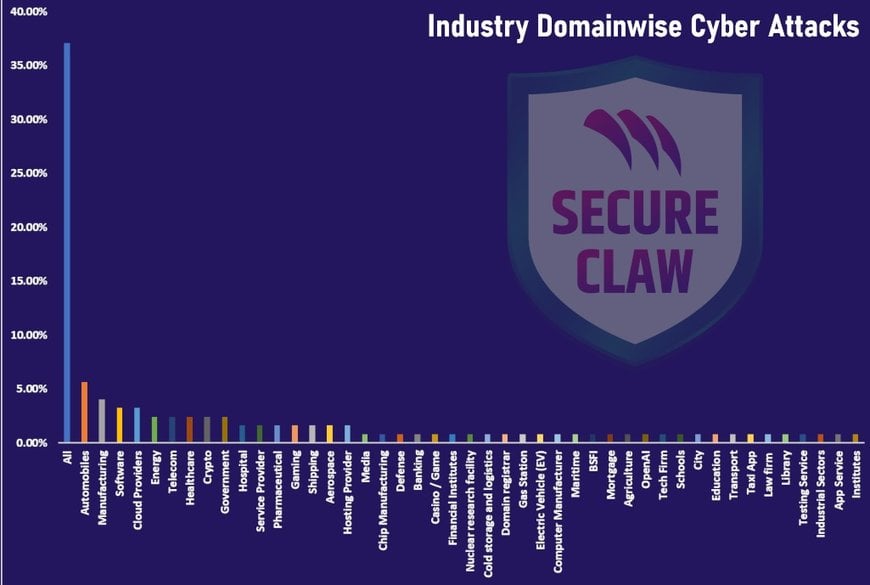
Industry-domainwise cyber-attacks
Few malware were very active in this period, such as Frebniis Malware, SwiftSlicer Widget, Emotet, Invicta Malware, Fluhorse Malware, Letscall Malware, Big Head, PDF-related malware, Backdoor-related malware, StripedFly, SysJoker Malware, and KV-Botnet. Researchers have uncovered a new, sneaky malware called "Backdoor.Frebniis", or simply "Frebniis". It uses an IIS weakness to create a backdoor into Windows web servers. Targets in Taiwan have been actively targeted by anonymous cybercriminals. Hackers must first gain access to an Internet Information Services (IIS) server in order to infect a system. The malware's internal mechanisms, however, are distinct. Failed Request Event Buffering (FREB) is a feature that IIS employs to gather information about requests, such as the originating IP address and port, HTTP headers containing cookies, etc. Frebniis abuses this feature. Before utilising the malicious iisfreb.dll module to take control of the FREB code, Frebniis first makes sure that the FRT feature is active. After that, it gains access to the IIS server process memory. The malware replaces the original FREB file, allowing Frebniis to intercept and examine each HTTP request from the IIS server in a "stealthy" manner. The backdoor interprets any string that is received encoded in Base64, which it believes to be executable C# code, and uses that interpretation to perform remote execution directly in memory. In this sense, Frebniis operates in an entirely covert manner by not storing any data as a physical file on disk. Similarly, each identified malware has its unique technique to perform malicious activities till actual cybercrime.
How to be more secure and have good cyber resilience?
The entire world is experiencing advancements in technologies like AI-ML, ChatGPT, automation, and quantum computing, whereas the other side, which is largely unethical practices, is also getting more benefits to increase cybercrimes, probably using the same technologies with different motives. As each one of us has seen the impact of the Coronavirus pandemic, it is time to ask, "Are our industries, businesses, or even personal assets prepared for any upcoming highly innovative computer virus kind of threat?" Each one of us should think about it, as I am sure many of us and our ecosystems are not even prepared for this. If such a thing really happens and one day all businesses or all electronic equipment stops working or starts malicious behaviour, it will be the biggest show stopper to the economy and many other things.
SecureClaw Cyber Threat Advisory, which keeps an eye on daily cyber threat news and alerts and tries to recommend solutions to companies worldwide, has studied more than 4,500 pieces of cyber news from across the world, appearing in leading cyber news forums and websites. Here are a few important statistics that are the outcome of the compilation of cyber news worldwide, considering the period from January to December 2023. Geography-wise, this data may differ from the actual cyber-attack statistics of a few countries, as at the ground level, many organisations from a few countries never report cyber incidents to authorities or news channels. Whereas the eagle eyes of our cybersecurity experts from SecureClaw have captured maximum cyber-attack news from many countries, it will give more insights about types of cyber threats and related information.

The various types of cyber-attacks
Key observations by SecureClaw
Apart from various industry domains, a few domains, such as automobiles, manufacturing, software providers, cloud providers, energy, telecom, healthcare, crypto, government, hospitals, pharmaceuticals, gaming, shipping, aerospace, and a few service providers, were mostly on the radar of cybercriminals throughout entire 2023. Most cyber threats were targeted at database systems, IT infrastructures, software systems, operational technology (OT), websites, servers, computer machines, emails, the cloud, APIs, ChatGPT, and mobile apps. Different techniques and sophisticated cyber-attacks were used via various types of data breach methods, including ransomware, malware, phishing, DDoS, unauthorised access, backdoors, integrity hacks, operational technology (OT) hacks, credential theft, spyware, SQL injection, insiders, and Trojan horses. The purpose of these cyber-attacks can be summarised as damaging reputations, disrupting business activities, hurting the competition’s business, extortion (financial demands), or illegal or unauthorised access to data. Also, few cyber-attacks seem to be state-sponsored, as there are wars and conflicts going on across the borders of a few countries.

Region-countrywise cyber-attacks
More advancement in cyber-attack techniques
Ransomware attacks in 2023 had negatively impacted a few large enterprises, including automobile companies Ferrari, Tesla and Volvo Cars; maritime information services company Royal Dirkzwager; Hitachi Energy; Taiwanese PC company MSI; the Suzuki motorcycle plant; multinational tech firm ABB; Japanese pharma giant Eisai Group; Spanish bank Globalcaja; chip giant TSMC; Japanese watchmaker Seiko; Johnson Controls; MGM casino; Chilean telecom giant GTD; British Library, and the attack on a South Korean anti-aircraft weapons system.
During these months, PlayCrypt (Play ransomware), Clop ransomware, Vice Society ransomware, Black Basta ransomware, LockBit ransomware, BlackCat/ALPHV ransomware, Snatch ransomware, Rorschach ransomware, and Rhysida ransomware were among hundreds of ransomware gangs that were more active in sophisticated cyber-attacks. Each of these ransomware gangs has a typical pattern they have developed for performing cybercrimes. Since June 2022, multiple victims of Play ransomware assaults have surfaced in Bleeping Computer forums. The ransomware named Play gets its name from the way it encrypts files: it adds the ".play" extension afterwards. The group's email address and the solitary word "PLAY" are also included in the ransomware note which is a unique pattern followed.

Assets under cyber-attacks
The Russian ransomware group Clop is well-known for its demand that victims pay millions of dollars before disclosing information that it says it has compromised. Vice Society is the next Ransomware-as-a-Service (RaaS) attacker targeting the education industry; move over, Lockbit. Vice Society is thought to be an extortion, exfiltration, and intrusion organisation with Russian roots. Vice Society is well-known for, like many other ransomware groups, stealing data from victims' networks prior to encryption in order to use it for double extortion. They then threaten to post the data on the dark web if the demanded ransom is not paid.
The Black Basta ransomware group, which has been active since April 2022, has been seen attacking American companies, concentrating mostly on the manufacturing and construction sectors. They have also been seen focusing on the real estate, food and beverage, chemicals, insurance, healthcare, and mining and metals industries, as well as business services. Malicious malware known as LockBit ransomware which encrypts files, renders them inaccessible, and demands payment for the decryption key. LockBit will automatically scan a network for worthwhile targets, disseminate the malware, and encrypt every machine that is reachable. Highly targeted attacks on businesses and other organisations are carried out by this ransomware.
Originally appearing in November 2021, BlackCat is a family of ransomware written in Rust, also going under the names ALPHV and Noberus. It also happens to be the name of the threat actor or actors that take advantage of it. BlackCat uses the RaaS business model, wherein the malware's creators provide it to affiliates for use and keep a cut of any money received in ransom. The Snatch ransomware, formerly known as Team Truniger, initially surfaced in 2018. Using RaaS, Snatch charges other threat actors for the ransomware payloads they supply. Snatch further employs double extortion by gaining access to their victims' private information. Snatch presses their victims to pay the ransom by threatening to expose the stolen material to the public if the requested ransom is not paid.
BabLock, also known as Rorschach, is a ransomware that has been making waves lately because of its fast-moving, sophisticated assault chain that employs deceptive yet powerful strategies. This ransomware was found to use an unusual method of attaching extensions in June 2022. Investigators found that, in contrast to the standard ransomware assault strategy of "one sample, one extension," the attackers for this particular infection were appending numerical increments ranging from 00 to 99 on top of the preset ransomware extension. Because of this, several extension versions may arise from a single execution even on an infected machine. Rhysida is a ransomware operation that targets Windows systems. It gained notoriety in May 2023 when it was connected to several high-profile cyber-attacks that occurred in Western Europe, North and South America, and Australia. There seems to be a connection between the group and the infamous Vice Society ransomware group.

Industry-domainwise cyber-attacks
Few malware were very active in this period, such as Frebniis Malware, SwiftSlicer Widget, Emotet, Invicta Malware, Fluhorse Malware, Letscall Malware, Big Head, PDF-related malware, Backdoor-related malware, StripedFly, SysJoker Malware, and KV-Botnet. Researchers have uncovered a new, sneaky malware called "Backdoor.Frebniis", or simply "Frebniis". It uses an IIS weakness to create a backdoor into Windows web servers. Targets in Taiwan have been actively targeted by anonymous cybercriminals. Hackers must first gain access to an Internet Information Services (IIS) server in order to infect a system. The malware's internal mechanisms, however, are distinct. Failed Request Event Buffering (FREB) is a feature that IIS employs to gather information about requests, such as the originating IP address and port, HTTP headers containing cookies, etc. Frebniis abuses this feature. Before utilising the malicious iisfreb.dll module to take control of the FREB code, Frebniis first makes sure that the FRT feature is active. After that, it gains access to the IIS server process memory. The malware replaces the original FREB file, allowing Frebniis to intercept and examine each HTTP request from the IIS server in a "stealthy" manner. The backdoor interprets any string that is received encoded in Base64, which it believes to be executable C# code, and uses that interpretation to perform remote execution directly in memory. In this sense, Frebniis operates in an entirely covert manner by not storing any data as a physical file on disk. Similarly, each identified malware has its unique technique to perform malicious activities till actual cybercrime.
How to be more secure and have good cyber resilience?
The entire world is experiencing advancements in technologies like AI-ML, ChatGPT, automation, and quantum computing, whereas the other side, which is largely unethical practices, is also getting more benefits to increase cybercrimes, probably using the same technologies with different motives. As each one of us has seen the impact of the Coronavirus pandemic, it is time to ask, "Are our industries, businesses, or even personal assets prepared for any upcoming highly innovative computer virus kind of threat?" Each one of us should think about it, as I am sure many of us and our ecosystems are not even prepared for this. If such a thing really happens and one day all businesses or all electronic equipment stops working or starts malicious behaviour, it will be the biggest show stopper to the economy and many other things.
A few important points on which businesses should focus
1. Adopt Cybersecurity Standard: Every organisation, starting from schools, colleges, manufacturing, maritime, chemical, pharma, information technology (IT), e-commerce, and even government organisations, should adopt cybersecurity best practices. Globally, today, 90% of the business population is small and medium businesses or enterprises (SMBs or SME companies), which are responsible for 60-70% of employment opportunities and 55% of GDP contribution in developed economies. If they are not able to adopt existing big cybersecurity standards, they should at least adopt the Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI) framework. This is easy to implement, less expensive, and, more importantly, provides tailored cybersecurity for the business domain of the company. Without structured cybersecurity implementation, it is difficult to reduce the cyber-attack surface for organisations. This should cover people, processes, and technology control areas.
2. Cybersecurity Awareness Training for Employees: The majority of cyber-attacks originate because employees do not have proper cybersecurity awareness. Good cybersecurity awareness training must be designed to cover many aspects, such as phishing attack precautions, policies, guidelines, insider threats, etc. Also, employees should undergo tests to check the effectiveness and delivery of the training. Few organisations can use phishing simulations to identify the impact of such cybersecurity awareness training.
3. Monitor Your Network: It is important to regularly monitor logs on the organisation's network devices and computers and even check notifications related to business transactions on mobile phones or emails. It will give hints on the malicious activities going on, so you can take action to prevent them.
4. Regular Security Audits: The organisation should invest in vulnerability assessment and penetration testing (VAPT), followed by fixation of the issues identified. Apart from technology assets undergoing VAPT, processes should be enhanced with time as per the organisation’s needs and compliances.
5. Track Incidents until Permanent Closure: Few incidents are alarming towards the possible harm to confidentiality, integrity, and availability of the critical assets of the organisation. It is important to track all possible incidents by preparing reports and taking the resolution towards permanent solutions.
6. Prepare BCP: Many organisations never prepare a business continuity plan (BCP) for any unseen circumstances, including natural disasters and cybercrimes. It is important to prepare for the worst. Also, organisations can test the effectiveness of such a BCP by executing cyber drills.
About the author
Dr Shekhar Pawar is a DBA in the cybersecurity domain at SSBM, Switzerland. He has completed his executive management degree from SJMSOM, IIT Bombay, and engineering in electronics and telecommunications from Mumbai University. Some of his skills and certifications include Certified Information Systems Auditor (CISA), Certified Ethical Hacker (CEH), Computer Hacking Forensic Investigator (CHFI), ISO 27001 – Lead Auditor, PCI DSS Implementer, Diploma in Cyber Laws, Microsoft Certified Professional (MCP), Certified Blockchain Developer, Certified ATM for CMMi Assessment, DSP & Applications – IIT Madras, and Diploma in Industrial Electronics. He is also the author of the nonfiction book ‘Air Team Theory: Understanding 10 Types of Teammates and Best Practices to Succeed’. Currently, he is working as Founder and CEO of SecureClaw Inc., USA, and GrassDew IT Solutions Pvt Ltd, Mumbai.

